PING allows you to know whether a machine is accessible via the internet
ping shows ICMP availability of the end point, which consist of the availability of hops in the middle and health of the endpoint.
Ping hostanme, no port as it doesn't allow port.
Telnet. ... Telnet enables a user to manage an account or device remotely. For example, a user may telnet into a computer that hosts their website to manage his or her files remotely. In the image is an example of a telnet session. As can be seen from this example, a telnet session is a command line interface
What Is Telnet? Telnet is a simple, text-based network protocol that is used for accessing remote computers over TCP/IP networks like the Internet. Telnet was created and launched in 1969 and, historically speaking, you can say that it was the first Internet
telnet <IP ADDRESS OF SERVER PC> <PORT>
What are the similarities and differences between ping and tracert? Ping tests the connectivity between devices but tracert does that in addtion to showing the path between the two devices
For Unix and Linux operating systems, the OpenSSH implementation comes free with the operating system and can be used to replace Telnet.
In the networking world, a default gateway is an IP address that traffic gets sent to when it's bound for a destination outside the current network. On most home and small business networks—where you have a single router and several connected devices—the router's private IP address is the default gateway.
Telnet is replaced with SSH: Telnet was deprecated in favour of SSH as Telnet sends credentials (username/password) in clear-text and any attacker on that network path can intercept the credentials. ... As it has been deprecated, it is typically still visible on legacy equipment, in particular network infrastructure equipment
What OSI layer is ping?
The ping command uses the services of the Internet Control Message Protocol (ICMP), the latter being encapsulated in the IP header. Therefore, the ping utility operates basically on layer 3 (the Network layer) of the OSI model.
What is ipconfig command?
Ipconfig (sometimes written as IPCONFIG) is a command line tool used to control the network connections on Windows NT/2000/XP machines. ... Ipconfig displays all current TCP/IP network configuration values and refreshes Dynamic Host Configuration Protocol (DHCP) and Domain Name System (DNS) settings
Internet Control Message Protocol (ICMP
BASIS FOR COMPARISON
|
TELNET
|
SSH
|
Security
|
Less secured
|
Highly secured
|
Uses port number
|
23
|
22
|
Data format
|
Telnet transfers the data in plain text.
|
Encrypted format is used to send data and also uses a secure channel.
|
Authentication
|
No privileges are provided for users authentication.
|
Uses public key encryption for authentication.
|
Suitability of network
|
Private networks are recommended.
|
Suitable for Public networks.
|
Vulnerabilities
|
Vulnerable to security attacks.
|
SSH has overcome many security issues of telnet.
|
Bandwidth Usage
|
Low High
| |
BASIS FOR COMPARISON
|
TELNET
|
FTP
|
Basic
|
It allows a user to log in to the remote server.
|
It allows a user to transfer a file to the remote machine.
|
Functions on Port number
|
23
|
21 and 20
|
Security
|
May have some security concerns.
|
More secure than Telnet.
|
Remote login
|
Is required to access the system resources.
| |
What layer is HTTP?
application layer
HTTP is an application layer protocol designed within the framework of the Internet protocol suite. Its definition presumes an underlying and reliable transport layer protocol, and Transmission Control Protocol (TCP) is commonly used.
What layer is FTP?
File Transfer Protocol(FTP) is an application layer protocol which moves files between local and remote file systems. It runs on the top of TCP, like HTTP. To transfer a file, 2 TCP connections are used by FTP in parallel: control connection and data connection.
Does Ping use TCP or UDP?
4 Answers. The standard ping command does not use TCP or UDP. It uses ICMP. To be more precise ICMP type 8 (echo message) and type 0 (echo reply message) are used.
They are TCP or Transmission Control Protocol and UDP or User Datagram Protocol. TCP is connection oriented – once a connection is established, data can be sent bidirectional. UDP is a simpler, connectionless Internet protocol. Multiple messages are sent as packets in chunks using UDP.
Is DHCP a TCP or UDP?
The DHCP employs a connectionless service model, using the User Datagram Protocol (UDP). It is implemented with two UDP port numbers for its operations which are the same as for the BOOTP protocol. UDP port number 67 is the destination port of a server, and UDP port number 68 is used by the client.
What OSI layer is DNS?
In OSI stack terms, DNS runs in parallel to HTTP in the Application Layer (layer 7). DNS is in effect an application that is invoked to help out the HTTP application, and therefore does not sit "below" HTTP in the OSI stack. DNS itself also makes use of UDP and more rarely TCP, both of which in turn use IP
Types of Protocols
- Transmission Control Protocol (TCP)
- Internet Protocol (IP)
- User Datagram Protocol (UDP)
- Post office Protocol (POP)
- Simple mail transport Protocol (SMTP)
- File Transfer Protocol (FTP)
- Hyper Text Transfer Protocol (HTTP)
- Hyper Text Transfer Protocol Secure (HTTPS)
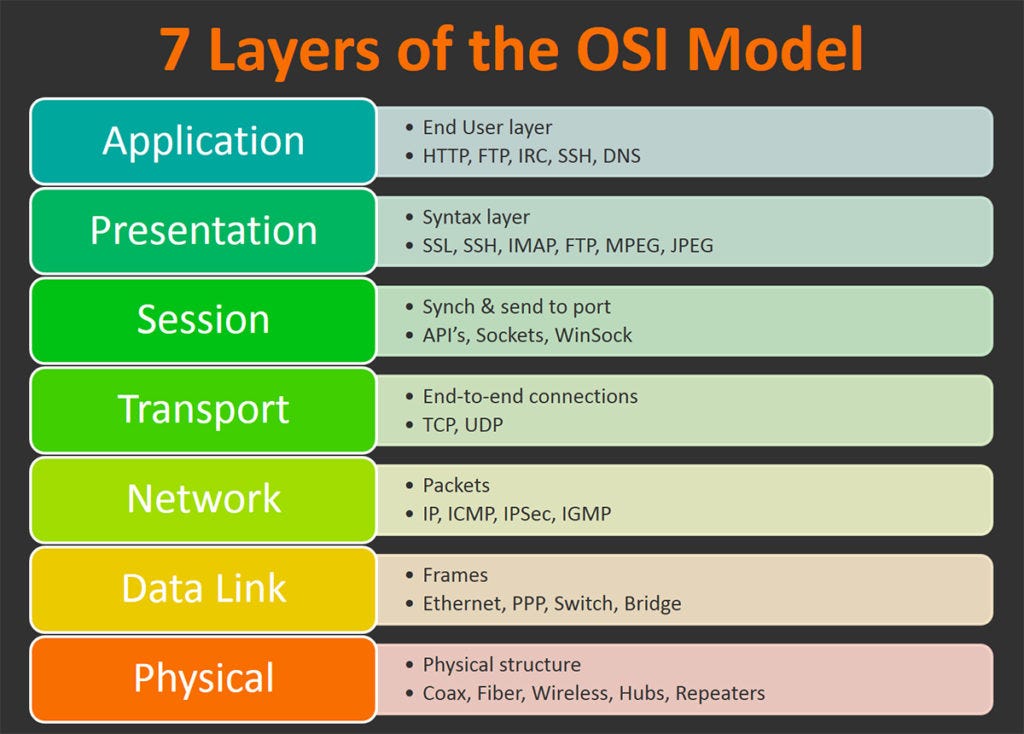
OSI model
| |||||
Layer
|
Protocol data unit (PDU)
|
Function[14]
| |||
Host
layers
|
7
|
High-level APIs, including resource sharing, remote file access
| |||
6
|
Translation of data between a networking service and an application; including character encoding, data compression and encryption/decryption
| ||||
5
|
Managing communication sessions, i.e., continuous exchange of information in the form of multiple back-and-forth transmissions between two nodes
| ||||
4
|
Reliable transmission of data segments between points on a network, including segmentation, acknowledgement and multiplexing
| ||||
Media
layers
|
3
|
Structuring and managing a multi-node network, including addressing, routing and traffic control
| |||
2
|
Reliable transmission of data frames between two nodes connected by a physical layer
| ||||
1
|
Transmission and reception of raw bit streams over a physical medium
| ||||
What port does ping?
Ping uses ICMP(Internet Control Message Protocol). it does not use TCP or UDP. To be more precise ICMP type 8(echo request message) and type 0(echo reply message) are used. ICMP has no ports!
What's the best DNS server to use?
List Of 10 Best Public DNS Servers
- Google Public DNS Server. This is one of the fastest DNS servers which many users are using on their computers. ...
- OpenDNS. Alongside Google's DNS servers, OpenDNS is one of the best cloud-based DNS servers. ...
- Norton ConnectSafe. ...
- Comodo Secure DNS. ...
- Level3. ...
- DNS Advantage. ...
- OpenNIC. ...
What is subnet mask in simple words?
A subnet mask is a number that defines a range of IP addresses that can be used in a network. ... A subnet mask hides, or "masks," the network part of a system's IP address and leaves only the host part as the machine identifier.
What is the format of IP address?
The format of an IP address is a 32-bit numeric address written as four numbers separated by periods. Each number can be zero to 255.
What port number is 8080?
GRC | Port Authority, for Internet Port 8080. Description: This port is a popular alternative to port 80 for offering web services. "8080" was chosen since it is "two 80's", and also because it is above the restricted well known service port range (ports 1-1023, see below).
What is the port 53?
Port 53 is used by the Domain Name System (DNS), a service that turns human readable names like AuditMyPc.com into IP addresses that the computer understands.
Netstat:
To find open ports on a computer, use netstat command line.
To display all open ports, open DOS command, type netstat and press Enter.
To list all listening ports, use netstat -an |find /i "listening" command.
netstat -an |find /i "3389"
Why would you use DHCP?
Dynamic Host Configuration Protocol (DHCP) is a network management protocol used to automate the process of configuring devices on IP networks, thus allowing them to use network services such as DNS, NTP, and any communication protocol based on UDP or TCP.
No comments:
Post a Comment